What is it?
BazarCall is a new attack methodology, known as a T.O.A.D (telephone-oriented attack delivery), which utilizes a phishing email to trick the victim into phoning a call centre - rather than clicking a link - and instructs them to download malicious file which infects their computers. By doing so, the BazarCall attack subvert common cyber security controls and allows the hacker to carry out a ransomware attack undetected.
The phishing emails usually refer to a subscription, for instance an antivirus software (see example below), which the victim never requested. The phishing email falsely claims that the only way to cancel this fake subscription is to phone the call centre.
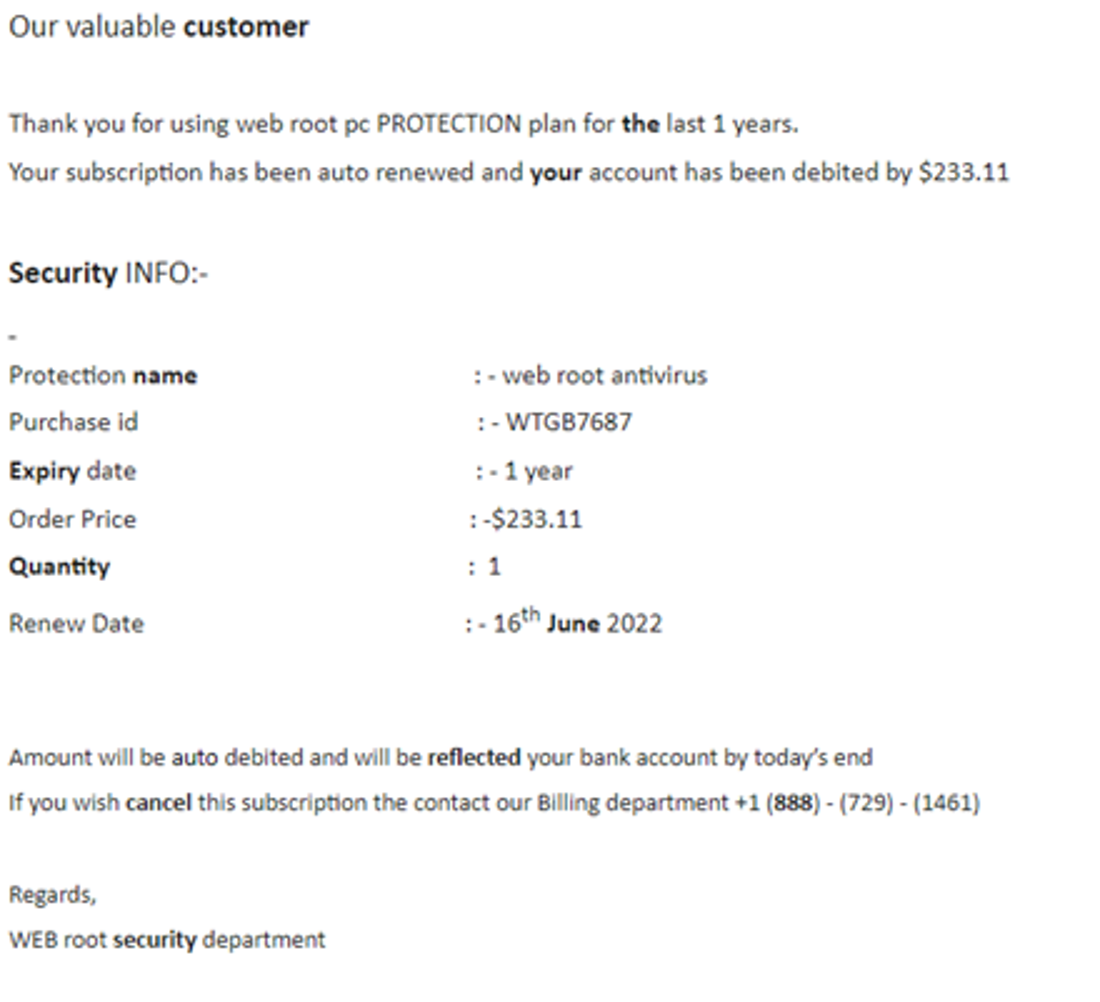
From there, the hacker verbally guides the victim through the process of downloading a malicious Excel file with macros and then enabling those macros, which in turn infects the computer with malware.
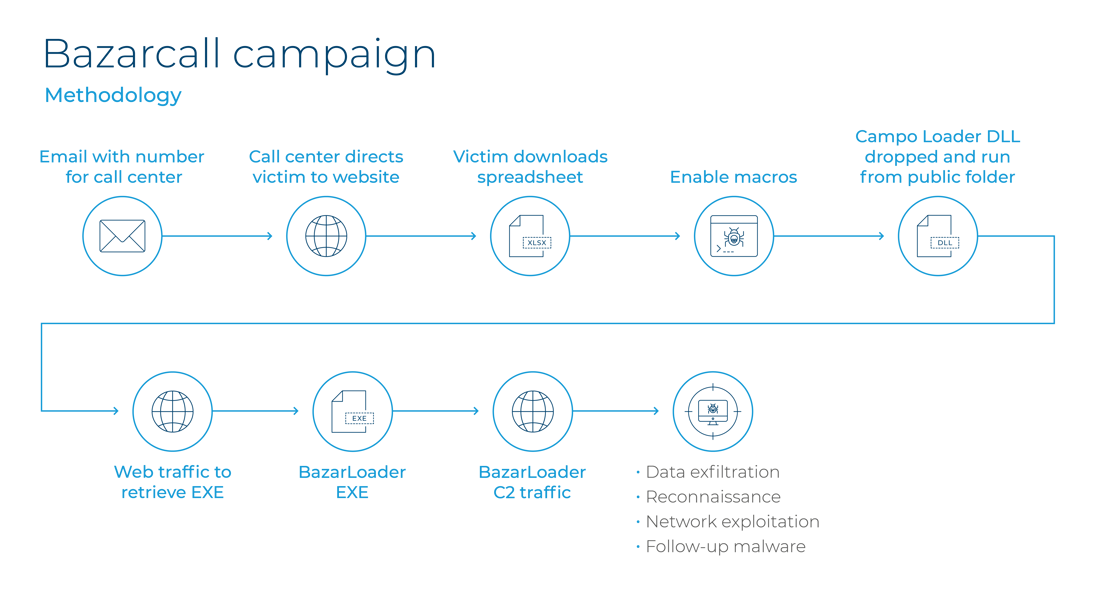
Bazarcall methodology. Source: Unit 42
Why is it critical?
Because the BazarCall method doesn’t require the user to click a link (as you would expect in a normal phishing email) common cyber security tools like email security filters can’t detect it. The method also subverts security controls because the user is downloading the malware themselves, unlike some more typical cyber attacks where the hacker must first penetrate the network.
Workplace security awareness education about phishing emails and social engineering doesn’t often include warnings for telephone-oriented attacks, which makes this attack more lucrative for hackers and more challenging for businesses.
What has CFC seen?
In early 2022, CFC’s cyber threat analysis team, which is responsible for analysing and responding to cyber threats on behalf of CFC’s cyber insurance clients, first observed an increase in adoption of this technique by a variety of well-known ransomware groups.
In response, CFC analysed its cyber customer base and found that BazarCall accounted for 10% of successful malware infections detected across its cyber portfolio in the last three months.
However, by intervening quickly, to date CFC has detected and removed every case of this malware within its impacted customers, at no cost to them. This intervention can happen at three stages:
- By identifying whether a specific victim has received the phishing email, but not called the phone number
- Whether they’ve called the phone number within the email
- Whether they’ve installed the malware
How to mitigate
In order to protect your business from such attacks it’s important you’re implementing the following:
- Keep all software and firmware up to date: Every device needs antivirus software. If an employee downloads a malicious application like the one from Bazarcall, or if an application becomes infected, antivirus software along with modern, up-to-date firewalls will help to secure the device and remove the infection.
- Implement multi-factor authentication (MFA) on all remote connections MFA can help reduce the amount of lateral movement and privilege escalation hackers can achieve within your systems. Even if your password is in the hands of the criminal, it is unlikely they will have your other forms of verification too. For more on MFA best practices, read our cyber tips piece on multi-factor authentication.
- Employee security awareness training: The majority of cyber attacks are the result of human error, particularly employees who inadvertently click on malicious links or fall victim to social engineering attacks like BazarCall. Carry out regular security awareness training with your employees and ensure it covers all types of social engineering attacks.
For other ways to keep your employees safe read our article, Staying Safe Online.
Other research on BazarCall:
Questions?
Should you have any further queries, please feel free to contact our team at cyberthreatanalysis@cfc.com



