To achieve the infection of a system, GootLoader hijacks Google search rankings to promote attacker-controlled websites further up in Google’s search index.
For example, typing the question, "the Canadian inter-company arbitration agreement" into Google presents this result for the attacker-controlled site on the first page:
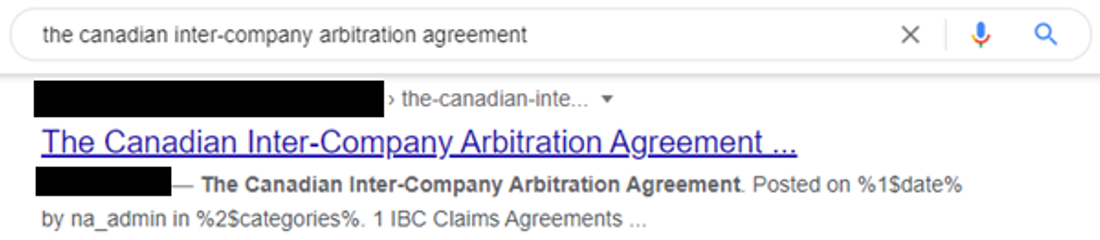
The website is for a marketing organization, which would not have anything to do with the search term. Clicking the webpage takes to you this forum post:
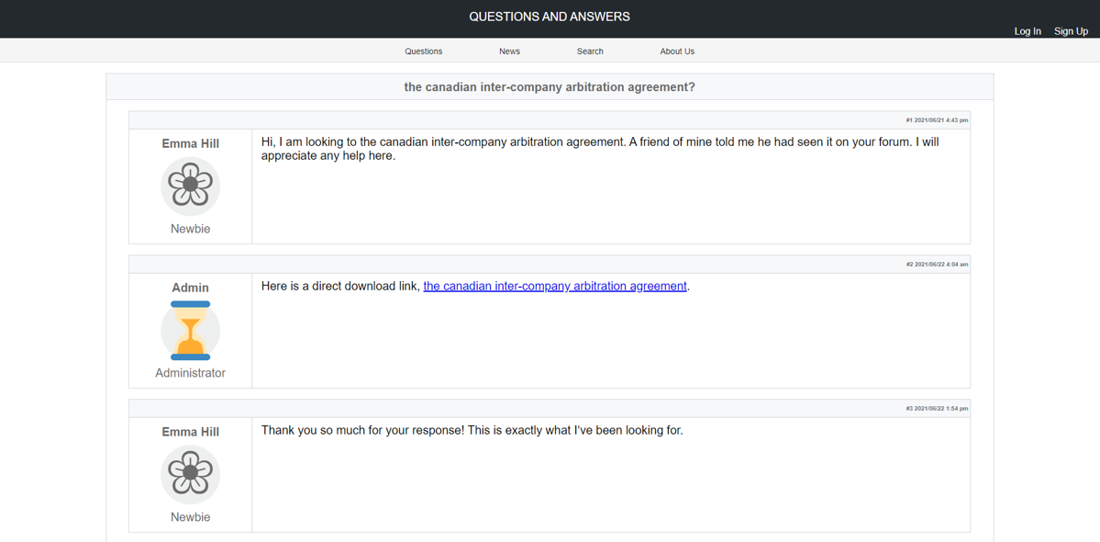
This page seems to deliver the exact answer to the question searched for and uses the exact same wording. Clicking the direct download link provides the visitor with a zip Archive (.zip) file which contains a JavaScript (.js) file also named to the search term. After double-clicking the malicious JavaScript file, the user becomes infected with GootLoader and an attacker can download further executables and malicious scripts such as Cobalt Strike modules in preparation for a ransomware attack. GootLoader has been notably seen in ransomware attacks originating from the REvil group.
The CFC Incident Response team has seen law firms’ websites which have been compromised to enable the distribution of GootLoader to other law firms visiting the compromised site. This is what is known as a watering hole attack.
What should you look out for?
We recommend sense-checking before downloading any file from the internet, but in recognition of this attack specifically you should ask yourself:
- Does the website topic seem to match the exact nature of your search term? In the example above, our search term was about a legal agreement but the website provided belonged to a marketing firm.
- Does the website require you to download the answer to your query? Attackers try to utilise compromised websites to encourage you to download malicious files.
- Does the page make grammatical sense? These pages are engineered to match your specific search term to encourage you to download the file, but don’t always make sense.
How can I protect my organization from these types of attacks?
- Ensure anti-virus and anti-malware solutions are set to automatically update and that regular scans are conducted.
- Ensure all operating systems and software applications are kept up-to-date and, where possible, have this done automatically.
- Consider investing in a secure web gateway to detect potentially malicious websites.
- Utilise device management tools to only allow trusted applications to run on devices, preventing users from running malicious executables.
- Ensure your users receive awareness training to decrease vulnerability to targeted attacks.
References:
https://news.sophos.com/en-us/2021/03/01/gootloader-expands-its-payload-delivery-options/amp/
https://www.areteir.com/dont-drink-from-that-gootloader-watering-hole-leads-to-revil-attacks/
https://www.ncsc.gov.uk/collection/supply-chain-security/watering-hole-attacks



